Once all the members of the distribution team are in position on the day of distribution, all possible questions or concerns from staff are addressed, the commodities are in place and beneficiaries have been assembled in the waiting area, the distribution can begin.
Registration/Verification
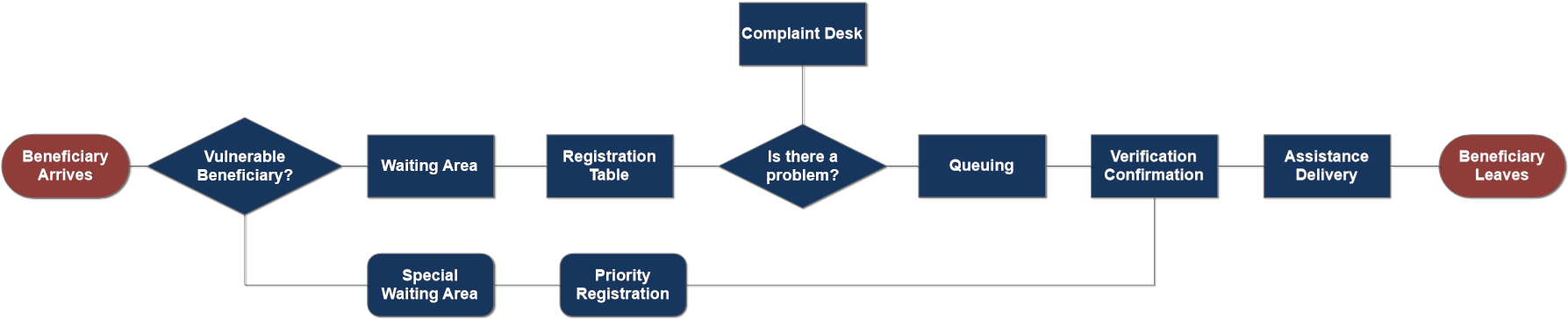
The first step during the distribution is the registration and control of beneficiaries. Registration is the stage where intended beneficiaries are confirmed as eligible. It is also the moment when the distribution team can ensure the distribution is documented and that the resources distributed have an identifiable beneficiary at the end of the chain.
Three different mythologies for registration exists:
- Manual Distribution Lists
- Distribution Cards
- Biometric/Digital Control
In order to prevent duplication and omissions of records, it is preferable that the registration and verification take place at the same time, assuring a proper segregation of duties between different parties. Programs with limited staff will often combine the process of collecting, processing and verifying registration data into one team. To minimise data manipulation and fraud, however it is important to segregate these tasks.
The staff responsible for registration/verification must assure the following steps:
- Train personnel involved in registration process, define team composition and division of tasks, consider potential challenges between the information collectors and respondents (such as language barriers and gender norms).
- Define roles and tasks (data collection, data cleaning, data processing and backing-up) in standard operating procedures (SOPs).
- Train teams on all elements of the participant registration process: data protection principles, informed consent and workflows.
- Explain the registration objectives and highlight any data security risks and mitigation strategies.
- Introduce SOPs and applicable protocols.
- Conduct a post-training skills check and address any knowledge gaps.
- Monitor the registration process and provide mentoring and feedback. At the beginning of the registration process, teams should regularly check the quality of data collected (i.e., blank fields, differing usage) to identify any gaps.
Manual Distribution Lists
Largely used for small to medium sized distributions in “one shot” interventions designed to tackle a specific need. This methodology consists of the collection and registration of beneficiary information manually on paper using a standard form to capture basic data. This simplified process facilitates the implementation and flow of ad-hoc/first time distributions, however, all the information gathered should be cleaned and processed manually at a later stage; as manual registration is prone to human error, the monitoring/reporting process may become cumbersome.
A manual distribution list will likely only contain beneficiary names and some household information, but no quantitative way to track individuals. Ideally, beneficiaries should produce some form of ID to match the list, but this is not always possible, especially in the early stages of an emergency. The manual list method also frequently utilises fingerprints or a signature as verification source, which cannot be verified in real time and largely can only be used for resolving claims of fraud or misuse after the fact.
Distribution Cards
Distribution cards are commonly used in camps or in situations in which cyclical distributions are common. Distribution cards are also useful when the beneficiary list is consistent. This methodology utilizes the creation and distribution of cards made from plastic or some other durable material. To facilitate this, organisations involved with distribution will intentionally identify Individuals or families who frequently receive distributed items though a formal registration process, and provide each individual or family with a distribution card. Distribution cards might include a serial number or ID code that refers to specific households containing all the information gathered during registration. The serial number or ID codes and correlating beneficiary information are maintained in separate system, usually an electronic database through which numbers can be quickly searched. Paper lists might be used in some situations where a computer database isn't accessible, but it is important that paper lists contain ID or serial numbers, and that data captured at the point of distribution is re-entered into a database later.
While a card system will require some investment on databases as well as time to gather information, prepare, issue and distribute the cards, this methodology greatly facilitates the registration process, especially if the card can be read by a bar-code or similar machine. Cards should ideally be accompanied by another source of verification at the time of distribution to assure the beneficiary identity.
Biometric/Digital Control
Biometric registration refers to the process of tracking recipients of distribution using unique biometric features of individuals. Biometric features might include fingerprints, eye, or facial features, all of which is automatically captured by recognition software and linked to the individual with a server-based database of beneficiaries. A biometric database might even be used at different geographic points if the beneficiary is migrating or mobile. While many biometric tracking systems are still developing due to high levels of sophistication and data management required, the use of this technology is increasing. A biometric system not only reduces input and duplication errors, but they also facilitate update, back-up, reporting, monitoring and auditing controls.
Any time biometric data is used to track beneficiaries, organisations should consider social and political implications of biometric tracking, and place protection concerns at the highest level. Information that can track an individual across multiple locations and time can also be used to target vulnerable persons, and may be the subject of scrutiny by law enforcement, armies and even non-state actors. Before implementing a biometric registration process, agencies should consult with protection professionals about concerns, and with local government bodies about laws governing gathering biometric data.
Safety
Security measures used in a distribution should be defined according to the risks involved. These risks can go from small-scale robbery to large-scale coordinated attacks and the same activity in different places will have different risk factor.
Distribution sites can quickly become chaotic, crowded and potentially dangerous places to both field staff as well as beneficiaries, particularly when there are long wait-times or commodity shortages. Security at distributions is usually the responsibility of government authorities. However, in some conflict situations, local law enforcement authorities cannot be viewed as neutral, and other crowd control mechanisms may be necessary. Once serious disorder has broken out there is little that humanitarian actors conducting distribution can do except to ensure the safety of the distribution staff, usually through evacuation.
Distribution teams can often prevent these situations through good site selection and design, through following operating procedures, and by positioning sufficient and trained crowd control personnel strategically throughout the site to facilitate flow, minimising long waiting periods to the extent possible, and dealing with fraud or cases of cheating in a quick and transparent manner.
During a distribution plan, program, logistics and security teams should work together to define such rules.
- The first layer of a security mitigation measure is community involvement: it is key to have local leaders supporting to spread the distribution rules and criteria. Special teams that communicate with communities also play a critical role in informing people about the activities and criteria of assistance.
- The presence of security forces should respect a strict progressive use of force approach when managing crowds. Force should only be applied when absolutely necessary, and in accordance with the level of threat.
- Have a prepared contingency plan and an evacuation strategy.
- Information is key: good visibility and constant community engagement help to keep people under control, especially in the case of shortages or changes in the food basket or distribution systems.
- Mind people’s minimum comfort needs: water, shade, access to sanitation.
- Appoint one person to be responsible for security decisions on the spot. Make sure that all other staff are aware of which person it is. He/shee should be easily visible.
- Provide staff with communication means like radios, whistles or establish another method to signal an emergency.
Complaint/Feedback Mechanism
It is important to acknowledge beneficiaries' concerns and complaints while referring those with specific problems to access the distribution services. A complaint or feedback system must be in place, ensuring complaints are recorded, documented and are addressed accordingly. A help-desk should be visible and be accessible without impediments, but also be away from the waiting area to ensure privacy and personalised support. It is advisable to appoint a representative from the distribution committee in the help desk. Any help desk should be able to converse in the language of the recipient population, and ideally be taken from the local community
It is important to differentiate between complaints and questions. Throughout a distribution, staff will very likely be approached by beneficiaries, authorities or others arising issues as:
- Lack of familiarity with distribution procedures and location.
- Lost, missing or incorrect ration cards.
- Faulty items or bad quality food.
- False claims in order to receive more items or food.
It is strongly recommended to brief the staff closest to the crowd about how to deal with questions and how to refer them to the help-desk if necessary. Efficiently responding to questions and complaints will have direct impact on the number of security issues likely to further arise.

